miek
#go
#pam
@linux
Using Go with PAM
miek
#fmt
#go
@linux
Automatically format Go HTML templates
miek
#neovim
@linux

Using the matchup plugin in Neovim for Go templates
miek
#go
@programming
Manual page creating with Kong
miek
#go
@programming
Fun things in Kong
miek
#ebpf
#bpf
#tinygo
@linux
eBPF code generation
miek
#ebpf
#bpf
#tinygo
@linux
eBPF target in TinyGo
miek
#ebpf
#bpf
#tinygo
@linux
eBPF target in TinyGo
miek
#ebpf
#bpf
#tinygo
@linux
eBPF target in TinyGo
miek
#ebpf
#go
@programming
eBPF in pure Go?
miek
#print
#android
@linux
Use CUPS to print IPP from Android
miek
#cfg
@linux
Config management: rolling back
miek
#cfg
@linux
Config management: microcode
miek
#osc52
@linux
Using OSC52 to enable remote cut and paste
miek
#cfg
@linux
Config management ideas
miek
#grafana
#dashboards
@linux
Dashboard generator for Grafana
miek
#gallery
#hugo
@meta
A Hugo gallery shortcode for images and videos
miek
#motd
#ascii
#art
@linux
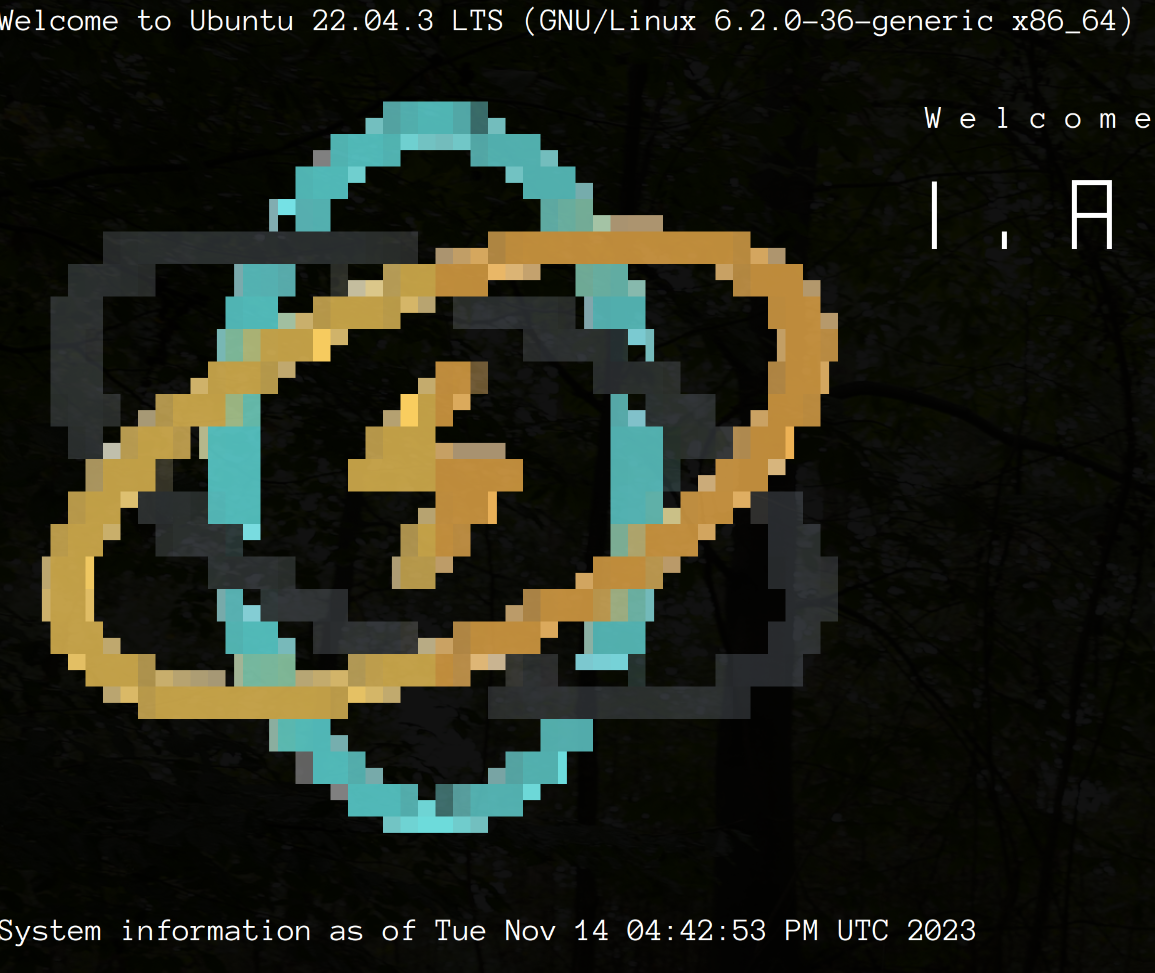
Create custom ASCII art for your /etc/motd
miek
#photo
@life

A Nice Morning view
miek
#dnssec
@dns
DNSSEC is too complex
miek
#neovim
#debian
#package
@linux
How to create Debian package from nvim source
miek
#internet
#ipv6
#freedom
@meta
IPv6 config for freedom internet


